HP PCs - Computer might be infected by a virus or malware (Windows 10)
This document explains viruses and malware, provides instructions for removing viruses and malware, and offers suggestions for preventing future infections. There are thousands of viruses, software programs, and security threats that can harm your computer, allow private information to be accessed by others, or make the computer perform slower.
Perform the steps in this document when the computer displays signs that it might be affected by a virus or malware, after the computer returns from service, or after running a system recovery. When the computer is serviced or when a system recovery is performed, the computer software is changed back to its original configuration, meaning it is set to the same condition as when the computer was first purchased. All software and driver updates that were installed on the computer, from the time it was first started, are lost. In this like-new condition, the computer is more susceptible to viruses because the added security updates have also been removed.
Note:
For business computers with antivirus and firewall configurations, a domain environment might have a specific configuration or scanner to assist. Inform your company's IT department or your local IT service of the issue, because they can make sure other users in the environment are protected.
Note:
HP SmartFriend is a support service that can help you strengthen security and resolve vulnerabilities on your computer. For more information, see HP SmartFriend (North America only).
Signs that your computer running Windows might be affected by a virus or malware
The following indicate that your computer might be affected by spyware, adware, or browser hijacking software.
-
The computer takes longer to start to the Windows desktop.
-
Applications do not load or frequently stop responding.
-
Frequent system error messages occur.
-
Unfamiliar icons are added to the desktop.
-
The system performs slowly, especially while browsing the Internet.
-
Browser windows close unexpectedly or stop responding.
-
The browser home page changes and cannot be reset.
-
Pop-up windows display more frequently and/or when the browser is not open.
-
Unfamiliar toolbars are added to the browser.
-
The default web search engine changes.
-
Clicking a web link does nothing or leads to an unrelated website.
-
Webpages are automatically added to your favorites list.
-
Email messages or social media posts are sent from your account without your knowledge.
-
Unexpected and near constant hard disk access occurs.
Turning on a firewall in Windows
Setting up a firewall provides basic protection against security threats before connecting to the internet. You can use Windows Defender or other firewall software, such as McAfee Personal Firewall.
Note:
Do not enable more than one firewall. Firewall software programs can interfere with one another if more than one is open.
Obtaining Windows Security updates
If you do not have a broadband connection that is always on or you want to check for updates, you can manually check for and install security updates for Windows Security.
Virus, spyware, and other malware definitions are files that Windows Security uses to identify threats to your computer. Microsoft regularly provides critical updates to make Windows more secure. These updates are important for protecting a computer. To keep these definitions up to date, Windows Security works with Windows Update to automatically install new definitions as they are released. If you have a broadband connection that is always on, set the Windows Update tool to automatically check for updates daily.
After the search completes, the updates automatically install.
Checking your computer for installed antivirus software
Many HP computers come with Windows Security or trial versions of other antivirus software apps already loaded. Before installing antivirus software, there are a few methods you can use to verify that your antivirus software is set up and running correctly.
Note:
Your computer might have come with a trial subscription to McAfee VirusScan or Norton Internet Security. HP recommends following on-screen prompts to renew your subscription. Renewing your subscription helps protect your system against new threats.
Verifying your security software by clicking the security icon in the Windows taskbar
Open the security software by clicking the software icon on the system tray area of the Windows taskbar.
Locating security software in Windows 10
If you could not find a security software icon in the system tray or you are still not sure if your computer has security software, check for security software in Virus & threat protection in Windows Security.
The security information displays.
-
If antivirus software is installed and enabled, see Updating antivirus software definitions in Windows.
-
If antivirus software is installed, but not on, enable the software, and then see Updating antivirus software definitions in Windows.
-
If antivirus software is not installed, see Installing antivirus software in Windows.
Installing antivirus software in Windows
If antivirus software is not installed, HP recommends you install antivirus software. New viruses are created and released often, and without antivirus software, the files and folders on the computer are at risk. If antivirus software is installed on your computer, you might need to update your antivirus software definitions.
Many HP and Compaq computers with Windows come with Windows Security. Other HP and Compaq computers might come with free trial versions of other antivirus software. These trial versions are usually limited versions that can be kept up to date for a specific period. After the period expires, your computer becomes more vulnerable to new viruses and security threats. It is important to upgrade or refresh the subscription to keep virus definitions current and continue protecting your computer.
If your device did not come with antivirus software, check with your Internet Service Provider (ISP). Many ISPs offer free or inexpensive antivirus software to their subscribers.
Note:
If you have antivirus software installed, but want to install different antivirus software, make sure to remove the old antivirus software before installing new software. Having multiple programs installed might make the computer slow, erratic, and potentially unprotected.
Updating antivirus software definitions in Windows
Because new viruses are created and released often, regularly update the virus definition files for the antivirus software. A virus definition file is a list of known viruses that the antivirus software uses to find and eliminate viruses.
The following steps offer a general overview for updating antivirus software, but if you need additional help, go to the antivirus software manufacturer website for more information. For a list of antivirus software support websites, see Security software support sites and other antivirus software (not HP).
For additional help with updating Windows Security definitions, see HP PCs - Using Windows Security to prevent virus and spyware problems (Windows 10).
Scanning for viruses and malware in Windows
After updating the antivirus software definitions, scan your computer for viruses and malware.
Usually, you can scan for viruses by opening the antivirus software and clicking a scan button. For steps to scan for viruses and malware using Windows Defender, see Scanning for and remove viruses and spyware from the PC (Windows 10).
If you do not use Windows Defender, go to the software manufacturer website for additional scanning help, as antivirus software varies. For a list of antivirus software support websites, see Security software support sites and other antivirus software (not HP).
Note:
If a virus is found and removed, open System Restore and delete any dates when the virus was active. This prevents the computer from accidentally becoming reinfected. Go to HP PCs - Using Microsoft System Restore for information about using Microsoft System Restore.
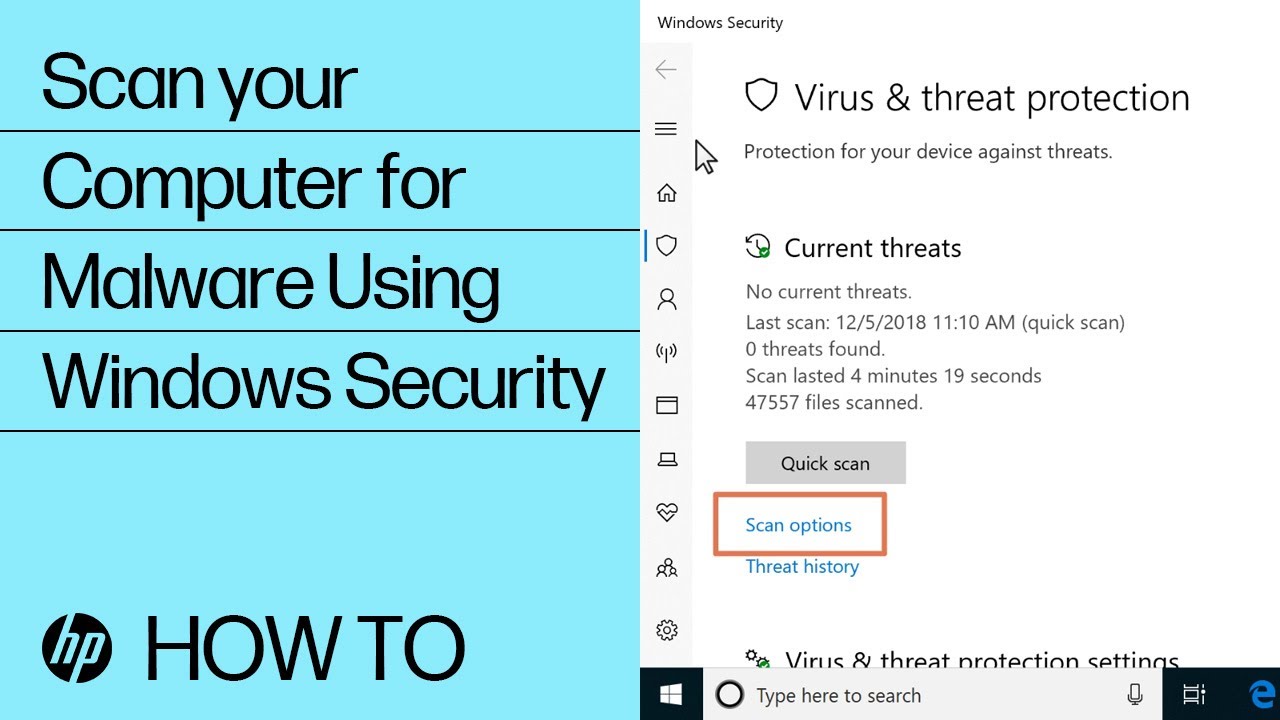
Scanning for and removing viruses and spyware from the PC
Use Windows Security to scan for and remove any viruses, spyware, or other malware from the computer.
-
Quick scan: A quick scan checks the places on the hard disk drive that malware is most likely to infect.
-
Full scan: A full scan checks all files on your hard disk drive and all currently running applications. If you suspect that malware has infected your computer, run a full scan. The scan might take over an hour to complete, and the computer might run slowly during the scan.
-
Custom scan: A custom scan checks specific computer drives and files that you select.
-
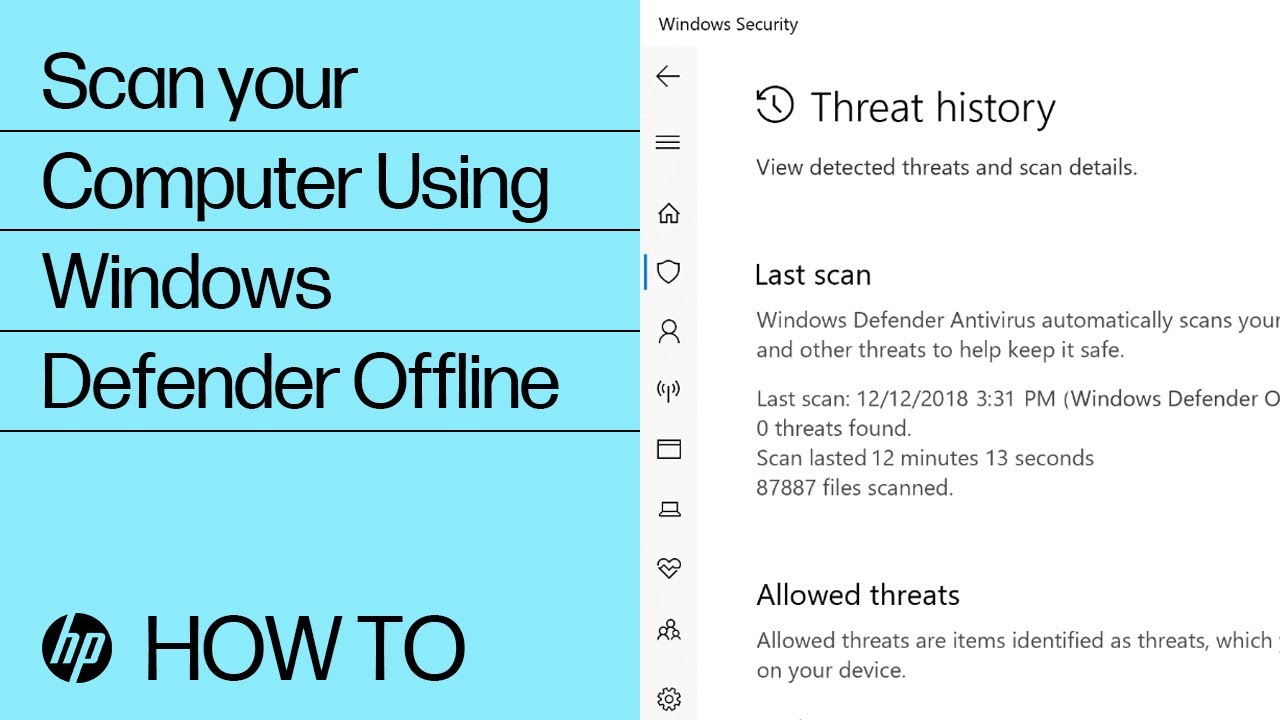
Windows Defender Offline scan: A Windows Defender Offline scan checks for rootkits or highly persistent malware on your computer. Select this option to check for malware outside of the normal Windows system. The scan might take 15 minutes to complete, and the computer restarts as part of the scan.
Note:HP recommends using the Windows Defender Offline scan if you suspect your computer is infected with malware or a virus.
Removing virus or malware by recovering the computer
If a virus is found, the virus might have already damaged or destroyed some files on the computer. The antivirus software might not be able to repair the damage. If the software cannot repair the damage, the computer might need to be fully recovered.
For more information, see HP PCs - Reset the computer.
Best practices for preventing virus and malware infections
You can avoid computer problems including viruses, spam, and spyware by using simple safety precautions when you connect your computer to the Internet. You can begin using the following security actions immediately.
Note:
HP SmartFriend is a support service that can help you prevent and remove unwanted software on your computer. For more information, see HP SmartFriend (North America only).
Detect and remove adware, spyware, and hijacking software with trusted professional removal software
Aggressive spyware and browser hijacking software can be extremely difficult to remove. Do not try to remove this software without the aid of spyware removal software.
Note:
You can manually remove most nonaggressive adware by uninstalling the software that it came with or removing the adware itself using Windows Add/Remove programs.
To remove aggressive malicious programs, use professionally developed products, such as Windows Defender. For more information, see HP PCs - Using Windows Security to prevent virus and spyware problems (Windows 10).
Prevent adware by buying full versions of known software
To prevent adware from being installed on your system, buy and use full versions of software that are not supported by advertising.
If you want to download and use software that claims to be free, carefully read the license agreement and cancel the installation if there is something that you do not agree to or understand. Know the software before you install it. The cost of installing such software might be slower Internet connection times, annoying pop-up ads, or an increase in unwanted emails (spam).
When you download a file, do not select Run to install the program from the web. Select Save, and then download the file to your hard drive. Before you install the program, test the file by right-clicking the file name, and then selecting an option like Scan or Scan for viruses to run the file through your antivirus software.
Before you install any program, read the End User License Agreements (EULA) carefully. Reputable companies tell you if they plan to install any adware or other background programs along with the software you want to use.
Be cautious of opening email attachments
Never open an attachment or a link in an email when you do not trust the sender. Sometimes a person intending to do harm sends an email message that appears to be from a trusted source, such as Microsoft. Most reputable companies do not attach software to email. If you do not trust an email, research it on the Internet or contact the company or sender named in the email.
Do not click on unfamiliar pop-up windows
To close a pop-up window in your web browser, click the X in the upper right corner of the window. If there is no X on the pop-up or browser window, press the alt and f4 keys at the same time to close the window.
Do not click any buttons within the advertisement, such as OK, Ignore, or Close, because you might not know what action is performed behind the button.
Do not click on security warning screens that pop-up from a webpage you do not know or trust
Read any pop-up messaging carefully before clicking on the window. Many times the message looks like an official warning to use some program or resolve a problem, but it can be an advertisement encouraging you to purchase an unnecessary program.
If you receive an official looking message or warning from a company, such as a bank or store where you have shopped, do not click any button to respond or verify receipt of the message. Call the company immediately, or open another browser and go to the company's official website to contact their customer service on the web. Criminals might be trying to steal information using a web URL that is similar to the company's official web address.
Often, spyware or hijacking software is installed when you "consent" to a security warning window that displays over a webpage. By clicking on a malicious security warning screen, a script or control is integrated into the browsing system. The script or control changes the behavior of your browser to suit the needs of the aggressive advertiser.
To prevent this from happening, never click anywhere inside a security warning window that displays with webpages you do not trust. Close these windows by pressing the alt and f4 keys at the same time.
Back up your data on a separate disk or online
To avoid file loss due to malware or virus infections, regularly back up your files on an external hard drive or online service.
For more information, see HP PCs - Back up your files (Windows 11, 10).
Protect your personal information
Never give out personal information (including email address, home address, phone number, bank account, or credit card number) unless you initiated the contact with the individual or company.
Remember, if you click on an ad that pops up, or a stranger contacts you on the web, you have no way of knowing who owns the website or how honest the person is.
CAUTION:
Do not give payment or personal information to callers who identify as HP employees and offer support. HP does not call customers and ask them to pay for support (for virus removal, for example). To learn more about phone scams, including what they are and how to avoid them, see the Microsoft support document Protect yourself from tech support scams (in English).
Disable suspicious add-ons in your browser
If professionally developed anti-spyware software cannot detect spyware software or add-ons, the spyware software might be new. Temporarily disable suspicious add-ons until you can update the anti-spyware software.
Disabling add-ons in Microsoft Edge
Disable add-ons in Microsoft Edge.
Disabling add-ons in Internet Explorer (8 or later)
Disable add-ons in internet Explorer.
-
From the Windows desktop, open Internet Explorer.
-
Click Tools or the Tools icon
, and then click Manage Add-ons.
-
Scroll through the list of add-on programs.
-
To disable an unwanted add-on, click the name of the add-on in the list, and then click Disable.
-
Click Close to close the Manage Add-ons window, and then close Internet Explorer.
Avoid threats by protecting your email address
Unscrupulous people can violate your privacy if you carelessly share your email information. As criminals use more sophisticated tools, you need to be vigilant in your daily activities. The following list describes methods criminals use to obtain your email address and offers strategies you can use to protect your information.
-
Chat rooms make it easy for people to harvest your email information.
Information like your account name and email address are available for anyone to collect when you are messaging in public chat rooms. Even if the site says "Private Chat Room", remember that there is no such thing as 'private' on the Internet. On these sites, every keystroke you make can be, and probably is being, recorded.
-
Posting your email address in comments in newsgroups or forums exposes your email address.
Email harvesters use software to automatically scour newsgroup and forum pages and record postings for email addresses. By compiling your email address and the topics of the forums, the harvester can determine your personal interests and browsing habits and then sell your name to marketing firms.
-
Posting your email address on forum pages results in more spam.
If an email address with the at sign (@) is posted on the site, the address is vulnerable. You can adopt the username AT InternetServiceProvider DOT com convention when posting email addresses in public forums to prevent harvesting.
-
Responding to spam or requesting that your name be removed from a mailing results in more spam.
When you respond to one spam email, the spammers add your address to every list. If you request that your name be removed, it is removed from that list, as required by law. However, it probably is added immediately to several other lists or sold to other spammers.
-
Forwarding a chain letter sends your email to other harvesters.
Chain emails include the addresses of all senders and receivers hidden inside the code. Email harvesters receive chain letters also, and your address can be added to their list.
Protect your identity with multiple email addresses
Protect your identity by using two or more email addresses when you respond to items on the web. Use one address for your friends and business associates, and use a different address for people and companies you do not know as well. Your ISP can provide you with a limited number of email addresses, but there are also many services that allow you to set up multiple free disposable email accounts.
-
For the free email account, make up a name with random letters and numbers rather than using your actual name.
-
If the free account gets loaded with spam and other unwanted material, you can close that account or just stop checking it.
Virus, spyware, adware, and browser hijacking definitions
There are many types of security vulnerabilities. Refer to the following list for definitions of common security threats.
To keep aware of the latest Windows threats and vulnerabilities, see Microsoft Security Bulletins (in English).
Viruses
A virus is a software program that copies itself into another program, a hidden space on a hard drive, or items that support scripts. Most viruses copy only themselves, while a minority deliver a payload.
A virus variant is a virus that has been altered to take advantage of the original virus program. Virus variants are easily created, resulting in new virus threats that must be monitored constantly by security programs, such as Windows Defender.
A payload is the action performed by malicious software such as a virus or Trojan. Payloads can damage files, deliver Trojan files, corrupt hard drives, display messages, or open other files. A payload activates when the file containing the malicious program opens. Often, a payload remains dormant until a certain condition occurs, such as when the date on the computer reaches a particular day.
Spyware
Spyware is software that gathers and transmits information without your knowledge. Spyware programs usually track information about websites visited, browser and system information, and your computer IP address (the number that represents a network device on the internet).
Adware
Adware is self-supporting software that displays ads while you are connected to the Internet. Most adware programs track how you browse the internet and report the information to an interested party.
Browser hijacking software
Aggressive advertising software can "hijack" your browser and make changes without your knowledge. These programs can be annoying and might resemble a virus at first (slow internet connection and lots of network activity).
Symptoms of browser hijacking software might include changes to your browser homepage, search bars or toolbars; new shortcuts added to your desktop; and advertising pop-ups. When a browser is hijacked, it might also redirect links to other sites that advertise or collect your usage information.
Worms
A worm is a type of virus that finds vulnerable computers and copies itself to those systems. The most frequent methods of spreading a worm are from email distribution lists, email signature scripts, and shared folders on a network. Worms might or might not have a damaging payload. The typical payload for a worm makes a computer more susceptible to other viruses and Trojans.
Trojans
Trojans are misleading software programs downloaded and installed from the web that appear to be safe, but are not. This type of software often comes from visiting a website that pops up a virus warning alert (even though the computer might not be infected). The pop-up suggests you purchase and install software to remove a virus or spyware, when, in actuality, there is no problem until you install the recommended software.
Some Trojans silently open malicious code that can log key presses, redirect web clicks, or even disable firewalls. Beware of programs that have similar names to popular legitimate security software, such as Windows AntiVirus, WinDefender, Norton Antivirus, System Defender, and McAfee LiveSafe.
Hoaxes
A hoax is an email claiming there is a threat to the security or functionality of the computer. For example, a hoax email might inform you that a virus is harming the computer when there is actually nothing wrong. Some hoax emails ask the recipient to perform a damaging process, such as deleting an important file. Most hoaxes are spread by people who do not know that the email is a hoax and who are hoping to alert others to a potential security threat or virus.
Phishing
Phishing is a method for fraudulently obtaining personal information. Phishing can come in the form of an email, or an internet link on a website or search engine results page that sends the user to a malicious website. When the user visits the website, the internet browser tries to read malformed code on the page and induces a security hole, or the webpage itself is designed to look similar to another legitimate webpage to collect credit card or other personal information.
Technical support scams
Technical support scams are a type of fraud where a person calls your phone or contacts you via a pop-up or email and pretends to have identified a problem with your computer. Do not give payment or personal information to callers who identify as HP employees and offer support. HP does not call customers and ask them to pay for support (for virus removal, for example).
To learn more about phone scams, including what they are and how to avoid them, see the Microsoft support document Avoiding technical support scams (in English).
Ransomware
Ransomware is a form of malware which encrypts files until a ransom is paid to the anonymous criminal who holds the decryption key. Most of the time the only available method to retrieve your files is to pay the ransom amount. It is very important to regularly back-up your data to protect against ransomware.
Security vulnerabilities
A security vulnerability is a weakness in a software program that allows unwanted activity inside the Windows operating system.
Security software support sites and other antivirus software (not HP)
Many trusted manufacturers provide support and antivirus software to help protect your computer.
-
Microsoft: Safety & Security Center (in English)
-
Check Point: ZoneAlarm Service and Support (in English)
-
Grisoft: AVG Anti-Virus (in English)
-
Kaspersky Lab: Kaspersky Technical Support and Knowledge Base: USA & Canada (in English)
-
McAfee: McAfee Support site (in English)
-
Symantec and Norton: Symantec Support (in English)
Enter a topic to search our knowledge library
What can we help you with?
Need Help?